Network Analysis – Malware Compromise
Scenario A SOC Analyst at Umbrella Corporation is going through SIEM alerts and sees the alert for connections to a known malicious domain. The traffic is coming from Sara’s computer, an Accountant who receives a large volume of emails from customers daily. Looking at the email gateway logs for Sara’s mailbox there is nothing immediately suspicious, with emails coming from customers. Sara is contacted via her phone and she states a customer sent her an invoice that had a document with a macro, she opened the email and the program crashed. The SOC Team retrieved a PCAP for further analysis.
What’s the private IP of the infected host? (4 points)
This one was preety easy. Looking at most of the source addresses, we see that 10.11.27.101 comes up alot.
From the Menu bar, Under Statistics, you can have a better view.
10.11.27.101
What’s the malware binary that the macro document is trying to retrieve? (4 points)
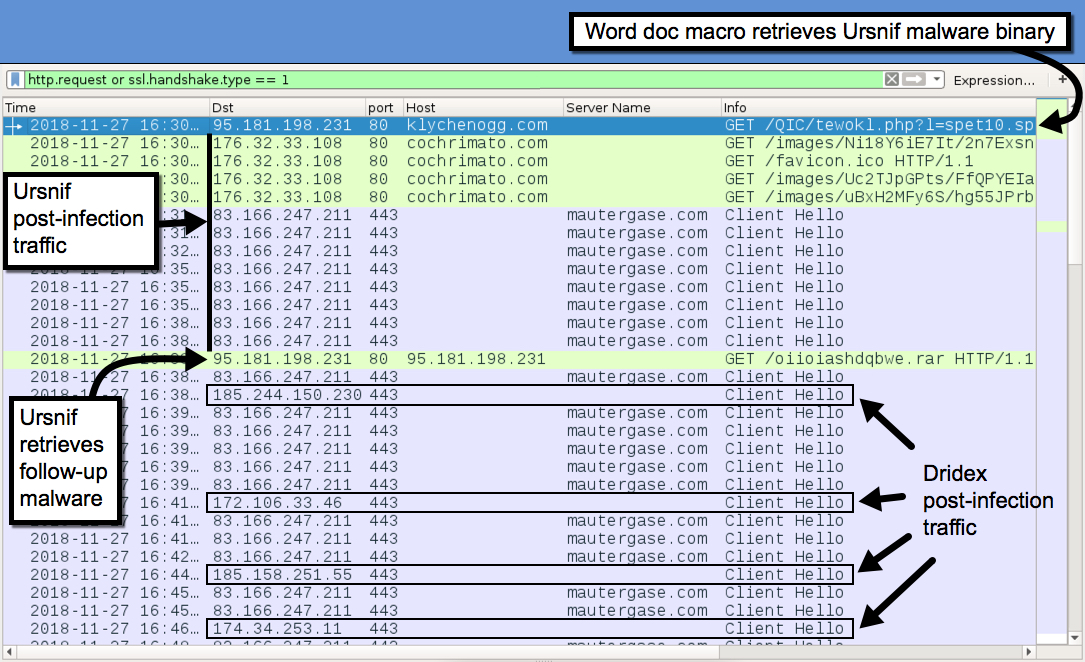
Headed over to File > Export objects > HTTP objects and you’ll find six packets with different filenames. Following the first packet 280,(tcp.stream.eq.0), we find one attachement with a file name of spet10.spr. Doing a quick google search, you will find other malware traffic analysis detecting it as Dridex malware. More information can be found here
spet10.spr
From what domain HTTP requests with GET /images/ are coming from? (4 points)
Filter out GET request using this filter:
http.request.method == GET
You’ll find 3 requests with an ip of 176.32.33.108. Looking at the GET request for one of the highlighted packets, we get the domain with the full request URI
cochrimato.com
The SOC Team found Dridex, a follow-up malware from Ursnif infection, to be the culprit. The customer who sent her the macro file is compromised. What’s the full URI ending in .rar where Ursnif retrieves the follow-up malware from? (4 points)
You can solve this question with some OSINT
In this case, lets stick to our pcap file. Earlier we saw in the export objects, a rar file called oiioiashdqbwe.rar. Inspecting the packet, we get a 200 with the full request URI
http://95.181.198.231/oiioiashdqbwe.rar
What is the Dridex post-infection traffic IP addresses beginning with 185.? (4 points)
To make this fast, on the menu bar, select Statistics and select Endpoints. on the IPv4 tab, you’ll easily see two IP’s starting with 185*. So manually filtering both ip’s i came to a close that 185.244.150.230 was used for post-infection traffic. Again, this can also be found here
185.244.150.230
Thanks for reading my write-up.😃 I would really appreciate it if i got your feedback on the same, like was it informative, too long, my grammar and use of terminologies was wrong?
Feel free to reach out to me on Twitter @oste_ke