PowerView Walkthrough
PowerView.ps1 can be found here
PowerView.ps1 can be downloaded here
Documentation
For more functions, check out:
Some Awesome Cheat Sheets
HarmJ0y also has a good article on using some of PowerView’s interesting functionality.
📝Personal Notes 📝
In the demo’s below, i have created an AD environment where my theme is inspired by the famous American sitcom “The Office”
I have then downloaded PowerView in one of my Windows 10 PC’s for practice Purposes.
First, you need to fireup your command prompt and type:
powershell.exe -nop -exec bypass
You then need to import the PowerView module as follows:
Import-Module [full path to powerview.ps1]
Alternatively, You could run:
powershell -ep bypass
Followed by:
. .\PowerView.ps1
From here we can start enumerating😉
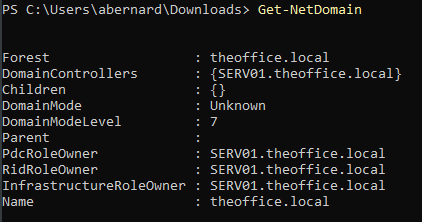
We can get information about the domain as follows:
Get-NetDomain
Getting information about DC’s
Get-NetDomainControllers
To query domain policies
Get-DomainPolicy
If you wanted to look at a specific policy, you would do so as follows:
(Get-DomainPolicy)."system access"
Information such as MinimumPasswordLength which shows 7 can enable you to know that we can try spray 7 character passwords
If we wanted to enumerate Users:
Get-NetUser
The above command spits a ton of information for all users. Assuming you are enumerating an organization with many users, this can generate a whole bunch of information. We can filter all users though by running:
Get-NetUser | select cn
or
Get-NetUser | select samaccountname
If we want to get all the groups a user is a member of
Get-DomainGroup -MemberIdentity username | select cn
or
Get-DomainGroup -MemberIdentity username | select samaccountname
If you wanted to check if the current user context has local administrator access
Invoke-CheckLocalAdminAccess
If you wanted to check if the current user has administrative access to the local (or a remote) machine
Test-AdminAccess
Lazy admins can leave behind some juicy details on the description. We can pull descriptions only by running:
Get-NetUser | select description
If we want to get all the groups a user is a member of
Get-DomainGroup -MemberIdentity username | select cn
or
Get-DomainGroup -MemberIdentity username | select samaccountname
To get all the effective members of a group:
Get-DomainGroupMember -Identity "Domain Admins" -Recurse
Get Information about all computers:
Get-NetComputer
Enumerating what operating systems are used on the domain
Get-NetComputer | select operatingsystem
Enumerating groups
Get-NetGroup This spits a ton of information
We can summarise all the information above by running
Get-NetGroup | select name
To locate shares on hosts in the local domain
Invoke-ShareFinder
To pull Group Policy Objects (GPO’s)
Get-NetGPO This spits a ton of information
We can narrow it down by selecting specific attributes. For example
Get-NetGPO | select displayname, whenchanged, whencreated
If you have any questions, comments or would like to reach out to me: