Network Analysis – Ransomware
What is the operating system of the host from which the network traffic was captured? (Look at Capture File Properties, copy the details exactly) (3 points)
To score this, you need to go the menu bar and select statistics and choose Capture File Properties. From here, you can easily get the OS information as shown in the screenshots below
32-bit Windows 7 Service Pack 1, build 7601
What is the full URL from which the ransomware executable was downloaded? (3 points)
Headed over to File > Export objects > HTTP objects and you’ll find one packet with an executable file called safecrypt. Manually exploring the packet, you’ll get the full URL in the GET request. Alternatively, you can choose to follow the http stream and get the answer.
http://10.0.2.15:8000/safecrypt.exe
Name the ransomware executable file? (2 points)
safecrypt.exe
What is the MD5 hash of the ransomware? (2 points)
On the linux terminal, you can use a tool called md5sum to get the hash. If you are solving this on windows, you can try tools like hashtab, hashtool among others. But inorder to get the hash, you need to export the executable we saw from the previous screenshot.
1
2
3
➜ md5sum safecrypt.exe
4a1d88603b1007825a9c6b36d1e5de44 safecrypt.exe
➜
4a1d88603b1007825a9c6b36d1e5de44
What is the name of the ransomware? (2 points)
In order to get the name, we can lookup if this hash has shown up in malware databses. Using Virustotal for example, we can search the hash of the binary or manually upload it. In this, we find various security vendors recognizing it as TeslaCrypt.
TeslaCrypt
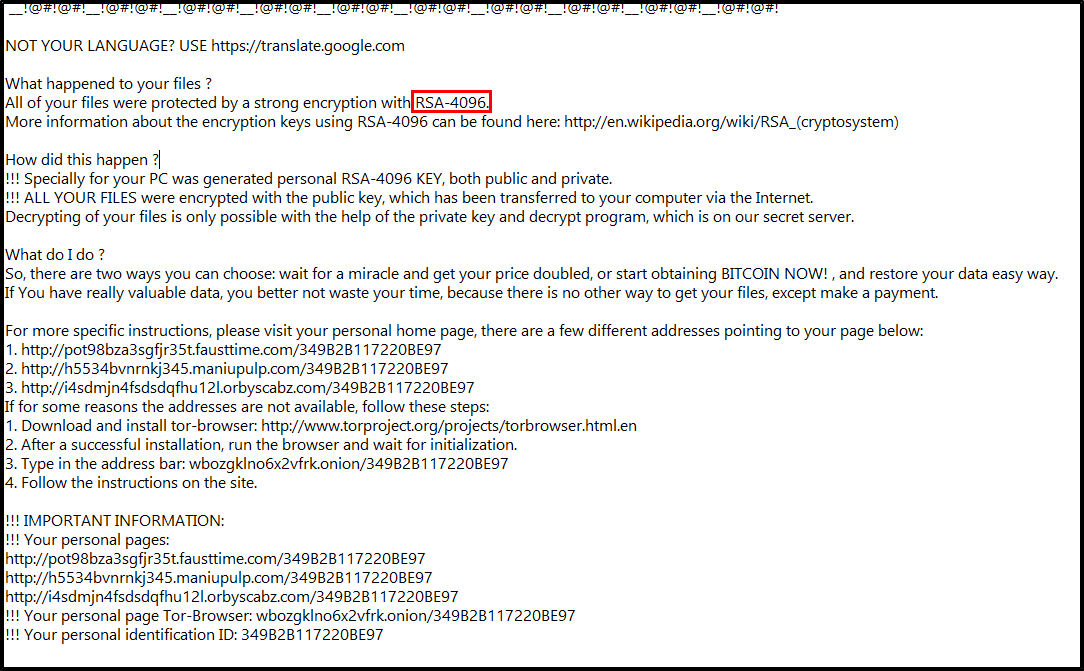
What is the encryption algorithm used by the ransomware, according to the ransom note? (2 points)
RSA-4096
What is the domain beginning with ‘d’ that is related to ransomware traffic? (3 points)
I filtered dns traffic then manually inspected the DNS query’s
dunyamuzelerimuzesi.com
Decrypt the Tender document and submit the flag (3 points)
I did some digging and found a command line tool that can decrypt files encrypted by the ransomware. You can download it at Mcafee. Instructions on how to use the tool can be found here. Decrypting was relatively easy and opening the document, we get the flag.
1
2
3
4
5
6
7
8
9
10
11
12
$ ./tesladecrypt.exe -h
usage: tesladecrypt.exe [-h] [--version] [-l] [-r] [-d] target_directory
positional arguments:
target_directory Directory to search for encrypted teslacrypt files
optional arguments:
-h, --help show this help message and exit
--version Get version information
-l, --list List all encrypted TeslaCrypt files
-r, --recursive Process files in sub-directories
-d, --del Delete encrypted files after decryption
1
2
3
$ ./tesladecrypt.exe -d E:\
>
Decrypting [ Tender.pdf.micro ] - OK and DELETED Encrypted File
BTLO-T3nd3r-Fl@g