
KnightCTF-2022
Hey there. I’m glad you are here. Here is a writeup of the challenges i managed to solve in the first Knight CTF - an online jeopardy style Capture the Flag (CTF) competition hosted by the Knight S...

Hey there. I’m glad you are here. Here is a writeup of the challenges i managed to solve in the first Knight CTF - an online jeopardy style Capture the Flag (CTF) competition hosted by the Knight S...
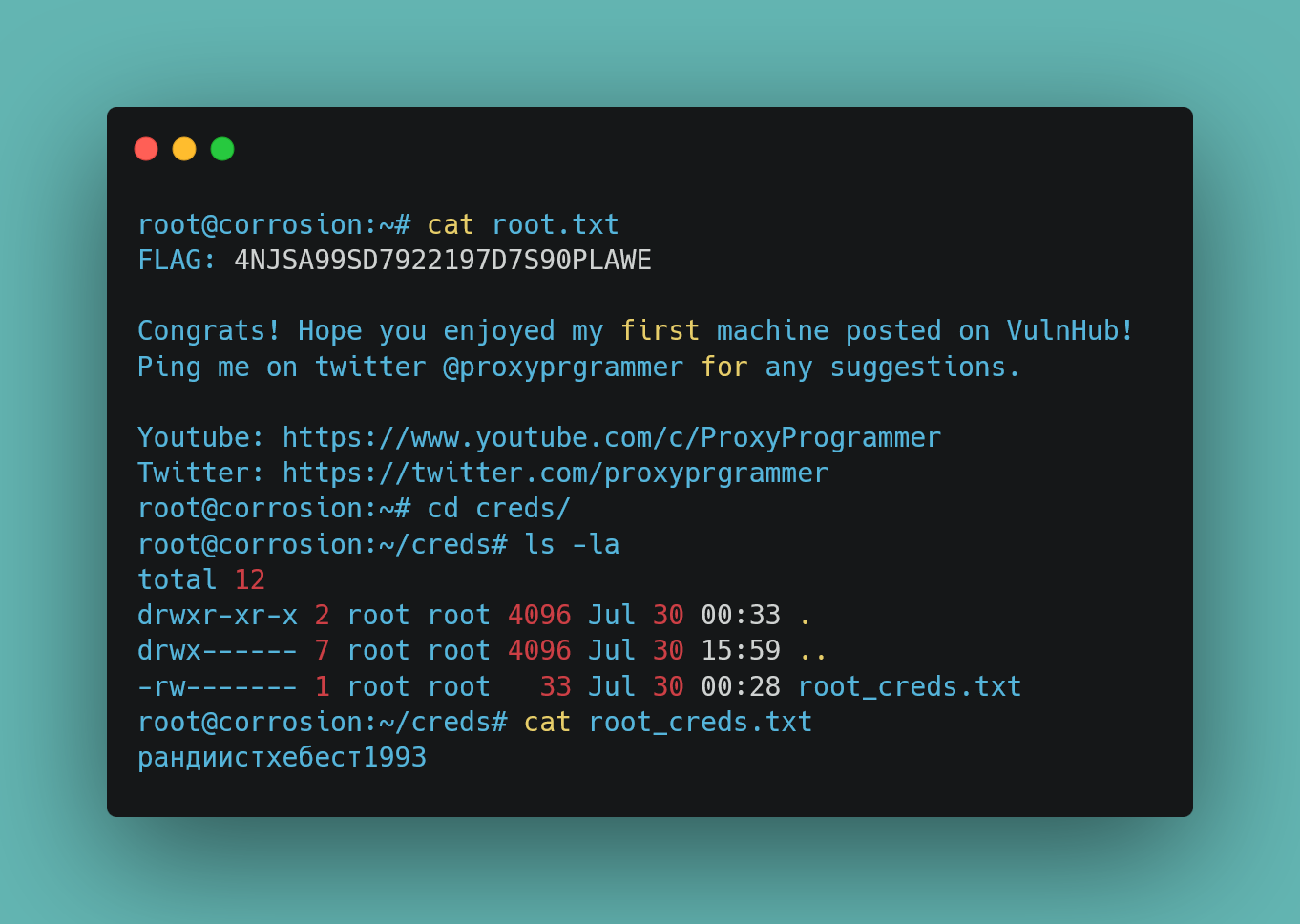
Machine Corrosion Author Proxy Programmer Difficulty Medium Series Corrosion Date release 2021-09...

Room Steel Mountain Author tryhackme Difficulty Easy In this room you will enumerate a Windows machine, gain initial access with...

Creating network While in Virtual Box, hold Ctrl+G to launch Preference. Alternatively, you can click the File tab and select Preference. Then click the Network tab and click the green icon wit...
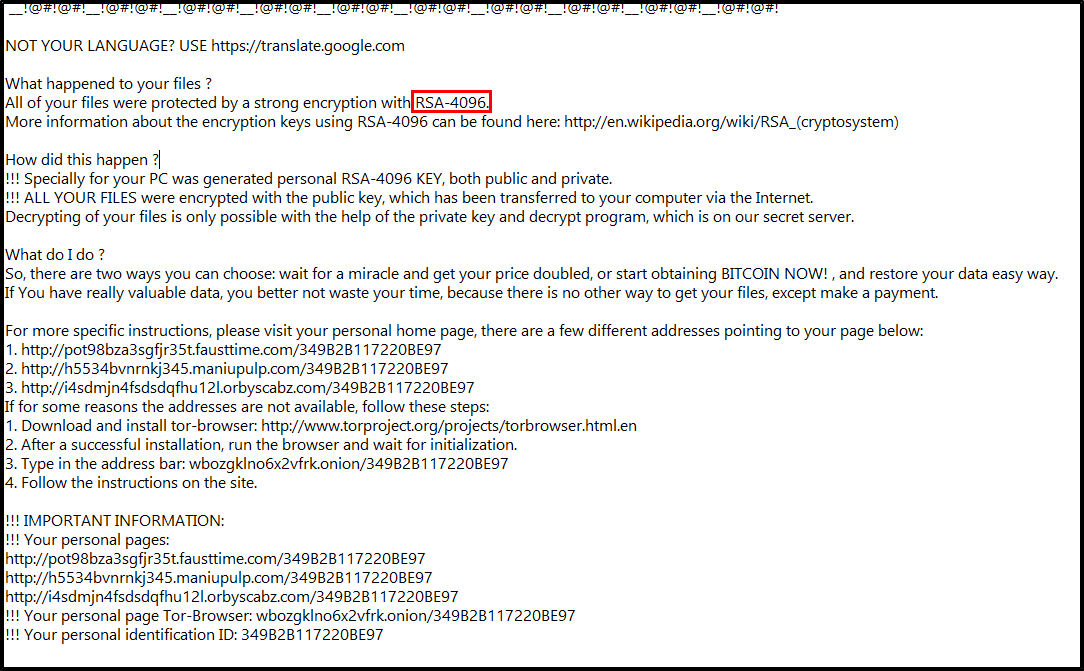
What is the operating system of the host from which the network traffic was captured? (Look at Capture File Properties, copy the details exactly) (3 points) To score this, you need to go the menu ...

Today we will be tackling a task from BTLO called Suspicious USB. At the time of writing, the challenge is retired. This was fun tackling and and researching new stuff that i was well acquinted wit...
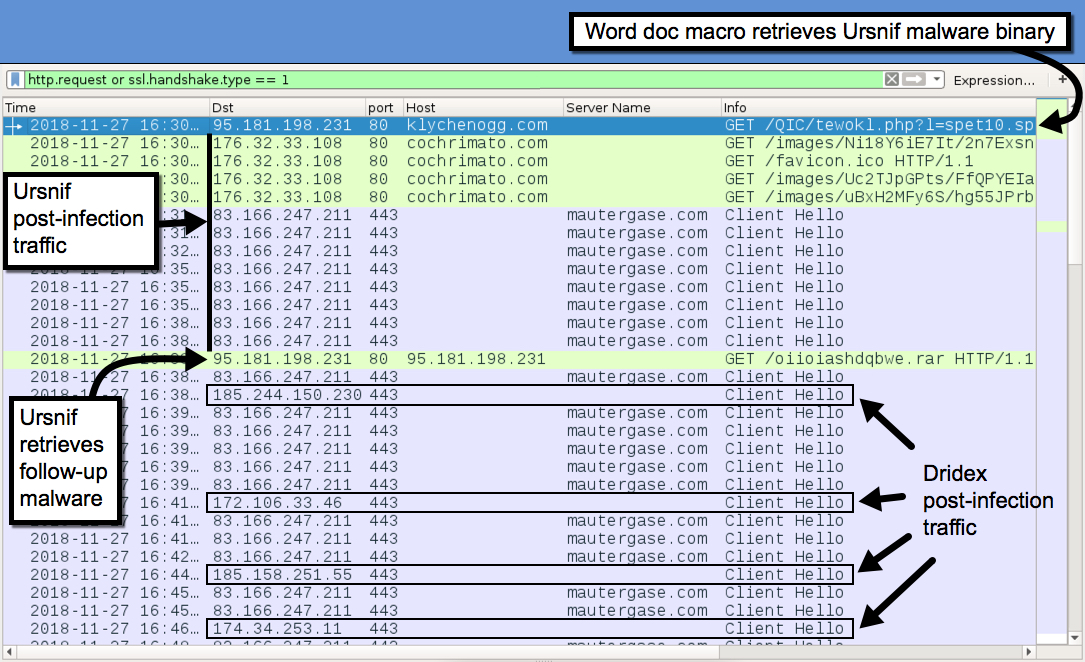
Scenario A SOC Analyst at Umbrella Corporation is going through SIEM alerts and sees the alert for connections to a known malicious domain. The traffic is coming from Sara’s computer, an Accountant...

Road Room Road Author StillNoob Difficulty Medium As usual, we first begin with a simple nmap scan to determine wha...

Today i’m going to be showing you how easy it is to have wordpress up and running using Docker Compose in an isolated environment built with docker containers. If you are not conversant with Docker...

In this walkthrough, i am going to show you how you can install docker on Ubuntu 20.04 in just 10 steps. However, minimal and cloud native OS are the preferred choice for a docker host since they a...